The following is a November 7 article titled “Next war could be a click away” by CNN Senior National Security Producer Larry Shaughnessy:
DARPA, the agency that really did invent the Internet, is now looking at ways the Web might be used to fight the next war. DARPA stands for Defense Advanced Research Projects Agency, a Pentagon office that researches everything from cutting-edge cybersecurity to hypersonic airplanes.
The agency’s director, Regina Dugan, told a gathering of cybersecurity experts Monday that “DARPA will focus an increasing portion of our cyber research on the investigation of offensive capabilities to address military specific needs.” In the past, the main focus of DARPA and other DoD cybersecurity offices has been defensive, protecting the Pentagon’s worldwide network of computers from hackers and “malware” – invasive software designed with malicious intent. Now DARPA is looking at how to reach out and attack, through cyberspace, the entities trying to break into and disrupt DoD computers. “To this end, in the coming years, DARPA will focus an increasing portion of our cyber research on the investigation of offensive capabilities to address military specific needs,” Dugan said. How much of a “portion?” Dugan says that in the next five years, the Pentagon, which is in the midst of massive budget cuts, will increase DARPA’s cyber-research budget by half a billion dollars.
Exactly how the Pentagon will use the Internet to attack adversaries is still unclear. Dugan didn’t say and didn’t take questions during the event Monday at a hotel near the Pentagon. Pentagon spokesman Capt. John Kirby wouldn’t elaborate on what the Pentagon might do. “Frankly it would be inappropriate for us to get into the details of specifically what we we’re looking at,” Kirby said. He did say that the options are wide open, since unlike the Geneva Convention that governs conventional wars, no similar agreements exist for cyberwar. “This is frankly a realm in which there are no international norms and no regulating policies internationally and it’s one we are trying to get our hands around,” Kirby said.
Cybersecurity goes well beyond well-known threats to privacy and the release of personal information. “Malicious cyberattacks are not merely an existential threat to our bits and bytes, they are a real threat to an increasingly large number of systems that we interact with daily, for the power grid, to our financial systems, to our automobiles and our military systems,” Dugan said. And that can happen in an instant. “A connected, motivated group can now accomplish tasks otherwise thought impossible, at speeds and scales that we are only beginning to understand,” said Dugan. How fast? Dugan used a non-malicious event to show how fast the cyber-world can move. “During the 5.9 magnitude earthquake that hit the East Coast on August 23 … there were almost 40,000 tweets within minutes and tweets from DC reached New York City ahead of the seismic wave itself.”
This research into possible Pentagon avenues of attack via cyberspace does not mean DARPA can let down its guard in terms of defending against cyberattacks. But the man in charge of stopping those attacks believes “cloud computing” represents a significant tool in protecting not only the Pentagon’s networks, but also its budget. “It’s easier to secure the cloud and there’s more than we can do with it,” said Gen. Keith Alexander the commander of U.S. Army Cyber Command.”I personally believe that taking a step towards the cloud is the right thing. It’s cheaper – we can come up with virtual networks, virtual routers, virtual databases, better encryption systems.” How much cheaper? In recent years, Alexander said switching to cloud computing has saved the DoD more than $100 Million in software licenses alone.
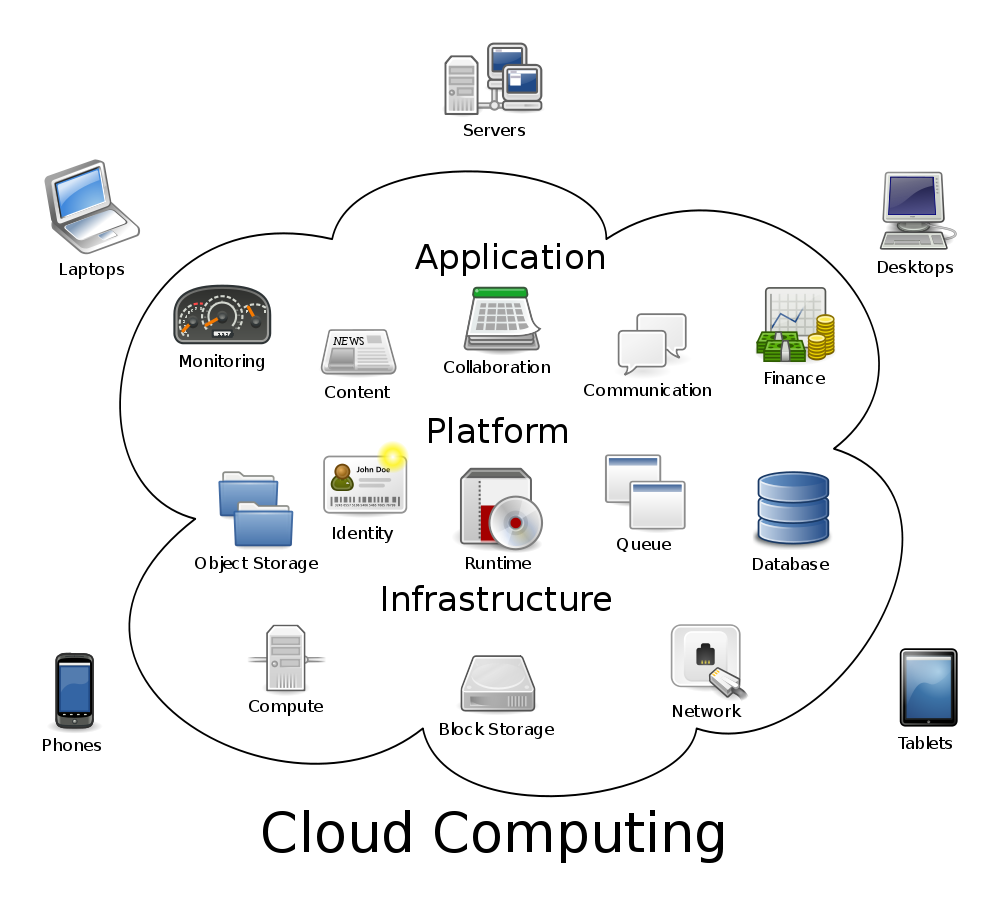
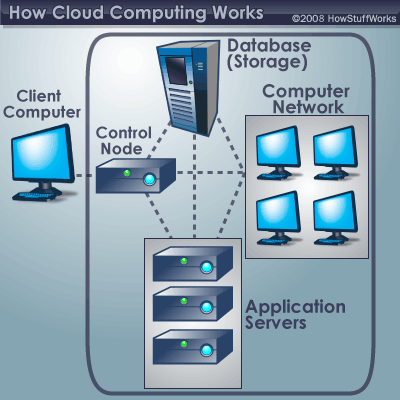
Editor’s note: For more on cloud computing and its pros and cons, see the Princeton article “What in the World is Cloud Computing?”